The news that an Android app from China was able to exploit a zero-day flaw on…
Continue ReadingTag: security

“Acropalypse” Android
The Android “Acropalypse” bug which has been around for the past couple of years has now…
Continue Reading
Security build
In a major funding round, Dope Security, a startup focused on secure web gateways, has raised…
Continue Reading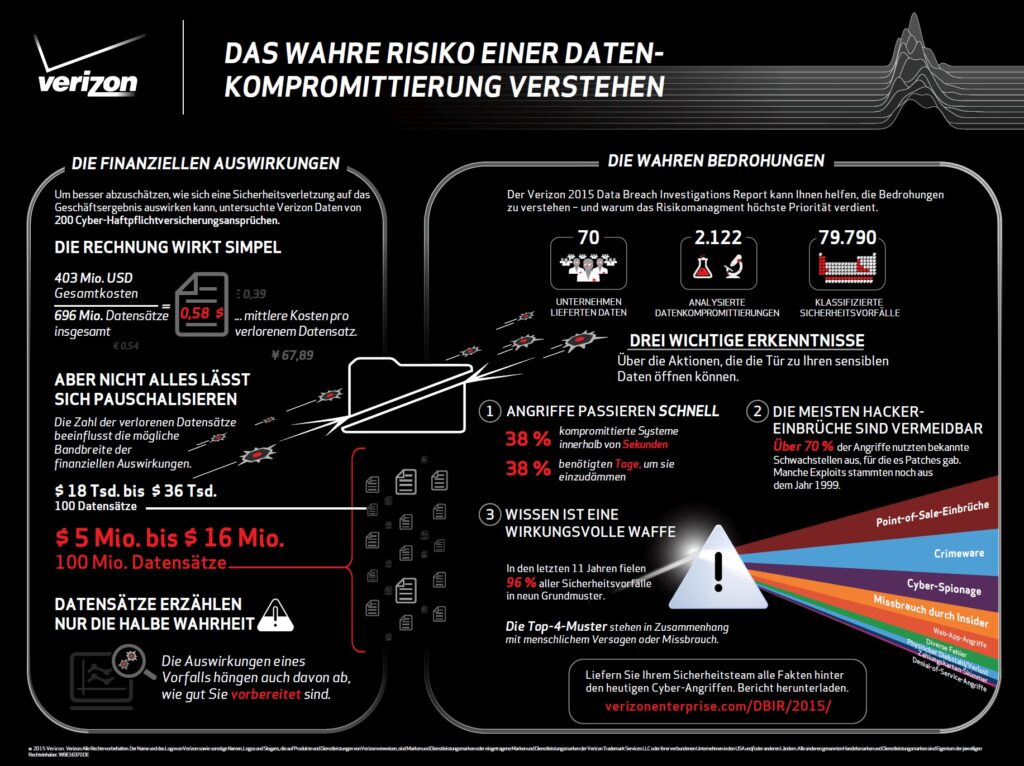
Security firm Rubrik is latest to be felled by GoAnywhere vulnerability
Recently, news broke that security firm Rubrik had become the latest victim of the ‘GoAnywhere’ vulnerability.…
Continue Reading
Web of lies: Web3 isn’t the security fix-all you think it is
Whether it’s for privacy, financial transactions, or data usage, we’ve seen many people turn to Web…
Continue Reading
North Korean hackers target security researchers with a new backdoor
In recent news, there has been an alarming revelation of North Korean hackers targeting security researchers…
Continue Reading
Signal CEO: We “1,000% won’t participate” in UK law to weaken encryption
The United Kingdom government wants tech companies which offer encrypted messaging services to weaken the security…
Continue Reading
This week’s Reddit breach shows company’s security is (still) woefully inadequate
It’s been a week since Reddit, one of the world’s most popular online platforms, experienced a…
Continue Reading
How to manage third-party cybersecurity risks that are too costly to ignore
As businesses become increasingly dependent on technology, they are often left vulnerable to security issues due…
Continue Reading
